Several different regulations, standards and legislation are practiced by various organizations and government agencies. Almost every country has its own national and state-level laws. The laws apply depending on where you live and where your data resides.
Let’s look at some of the regulations and standards.
General Data Protection Regulation (GDPR)

GDPR is the European Union (EU) directive that replaces the previously existing regulation known as the Data Protection Directive. The key focus of GDPR is to regulate how organizations should protect the data of the EU citizens. GDPR also focuses on the data movement outside the EU.
There are seven principles of GDPR:
Lawfulness, fairness and transparency
Purpose limitation
Data minimization
Accuracy
Storage limitation
Integrity and confidentiality (security)
Accountability
National, Territory, or State Laws
Depending on the country you live in, there can be national, territory, or even state laws for security.
For example, the United States has several laws that are applicable at the national level.
Some of the key ones are:
US Privacy Act of 1974: applicable to government agencies for the data they hold.
GRAMM-LEACH-BILLEY ACT (GLBA): focuses on protecting financial non-public information.
Health Insurance Portability and Accountability Act (HIPAA): focuses on protecting healthcare information.
Children’s Online Privacy Protection Act (COPPA): focuses on protecting the personal information of children below the age of 12.
Federal Information Security Management Act (FISMMA): provides the mandates to the federal agencies to protect data.
While the above-listed laws are at the national level in the United States, the other nations also have similar laws in place. For example, here are some national laws from the United Kingdom (UK):
The Computer Misuse Act of 1990
The Data Protection Act 1998
Regulation of Investigatory Powers Act 2000
Fraud Act 2006
Forgery and Counterfeiting Act 1981
Copyright, Design, and Patents Act 1998
Laws can also be specific to a territory or state. For example, the state of California in the United States has implemented the Notice of Security Breach Act. This act states that if an organization maintains the personal information of the California citizens and is a victim of any security breach, the organization must disclose the incident. There is then action taken on the organization. This act intends to ensure that the organizations invest in their security infrastructure to safeguard California citizens’ personal information.
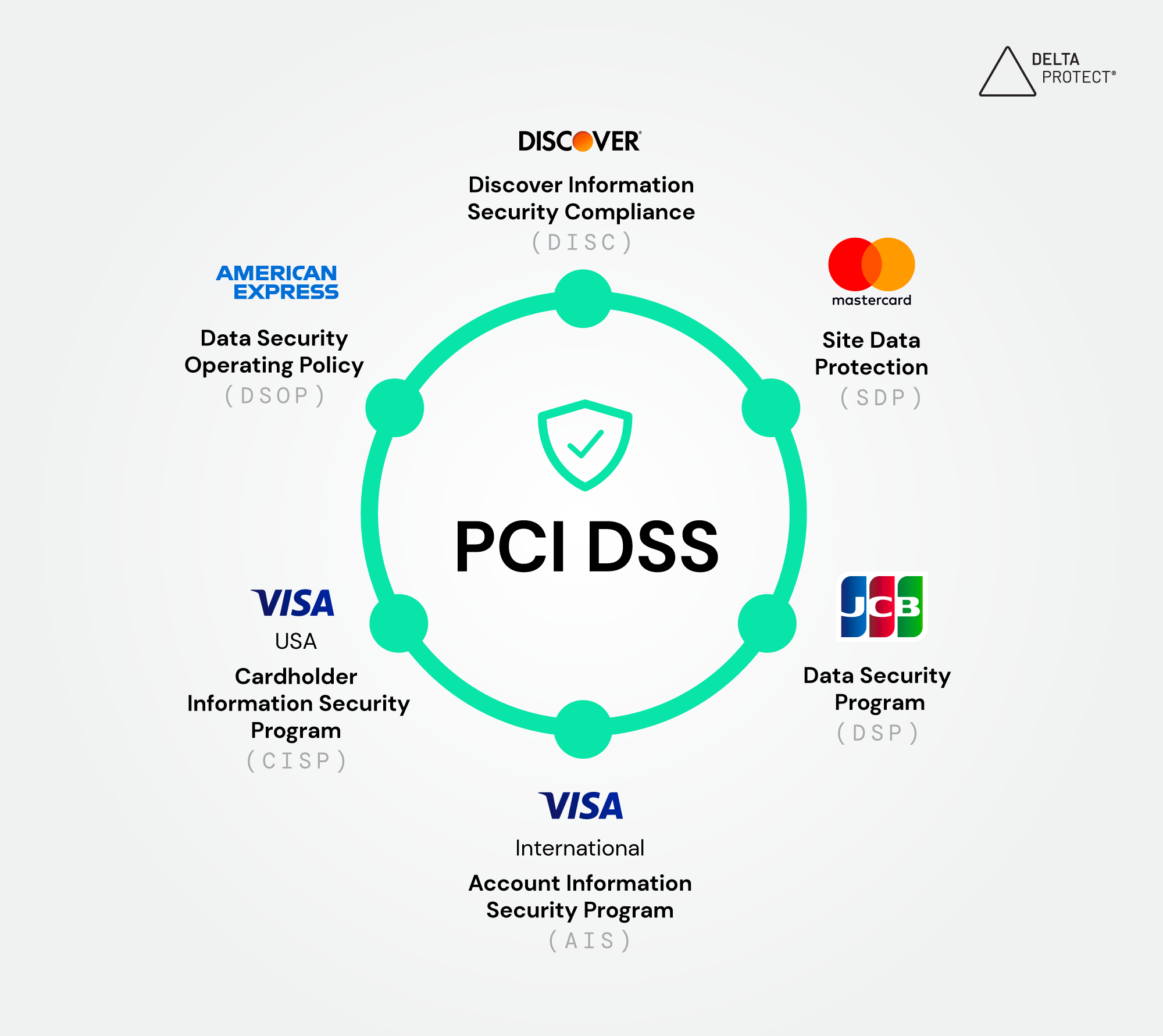
Payment Card Industry Data Security Standard (PCI-DSS)

PCI-DSS is a regulatory framework for organizations that deal with credit or debit card payments on the Internet. This is specific to the credit card industry.
Key Frameworks
A framework, or a security framework, defines a set of processes and procedures to help an organization implement security controls, which are meant to reduce the security risks. A framework can be specific to an industry or generalized to meet more generic requirements. For example, PCI-DSS is a regulatory framework for an organization that deals with credit or debit card payments on the Internet. On the other hand, ISO 27001 is a more general regulatory framework that can help any organization of any size to define an information security management system (ISMS).
The whole intent of a framework is to use the pre-defined guidelines. When you use a specific framework, you do not need to create the basic structure of policies and processes. However, it is important to note that a framework can always be customized to meet an organization’s needs.
There are several frameworks available in the IT industry, and most of them are designed with the security aspect in mind. Broadly categorizing, there are two types of frameworks: prescriptive and risk–based.
Center for Internet Security (CIS)

CIS is a non-profit organization that works in the area of Internet security. It has developed various benchmarks and guidelines for securing devices, platforms, and applications. There are CIS controls, which contain the following 20 security measures:
Inventory of Authorized and Unauthorized Devices
Inventory of Authorized and Unauthorized Software
Secure Configurations for Hardware and Software on Mobile, Laptops, Workstations, and Servers
Continuous Vulnerability Assessment and Remediation
Controlled Use of Administrative Privileges
Maintenance, Monitoring, and Analysis of Audit Logs
Email and Web Browser Protection
Malware Defenses
Limitation and Control of Network Ports, Protocols, and Services
Data Recovery Capability
Secure Configurations for Network Devices such as Firewalls, Routers, and Switches
Boundary Defense
Data Protection
Controlled Access Based on the Need to Know
Wireless Access Control
Account Monitoring and Control
Security Skills Assessment and Appropriate Training to Fill Gaps
Application Software Security
Incident Response and Management
Penetration Tests and Red Team Exercises
National Institute of Standards and Technology (NIST) RMF/CSF

RMF stands for Risk Management Framework that can help organizations assess and manage risks.
CSF stands for Cyber Security Framework that has several steps that need to be implemented. These steps and their tasks include:
1. Prepare: Organizational communication, development of control baselines, enterprise architecture, and alignment with RMF.
2. Identify: Asset management, business environment, governance, risk assessment, and risk management strategy.
3. Protect: Access control, awareness and training, data security, information protection processes and procedures, maintenance, and protective technology.
4. Detect: Anomalies and events, continuous security monitoring, and detection processes.
5. Respond: Response planning, communications, analysis, mitigation, and improvements.
6. Recover: Recovery planning, improvements, and communications.
International Organization for Standardization (ISO) 27001/27002/27701/31000

ISO is an independent organization that develops standards and frameworks that are deployed internationally. ISO has standards across various domains, such as:
Environmental
Food Safety
Health and Safety
IT Security
In the IT Security domain, ISO has various standards. Some of the key ones are:
27001: provides the requirements for an information security management system. ISO 27001 is a more of a general regulatory framework that can help any organization of any size. It helps an organization to define an information security management system (ISMS).
27002: focuses on security techniques and codes of practice for information security controls.
27701: is an extension to 27001 and 27002. It provides various guidelines for privacy information management.
31000: focuses on risk management. It provides various guidelines for managing risks within the organization.
SSAE SOC 2 Type II/III

SSAE stands for Statements on Standards for Attestation Engagements. SOC stands for Service Organization Control. There are SOC 1, 2, and 3 reports.
SOC 1: focuses on internal controls over financial reporting.
SOC 2: focuses on various controls, such as security, privacy, availability, and integrity. This report is available to regulators and those who sign the Non-Disclosure Agreement (NDA).
SOC 3: focuses on various controls, such as security, privacy, availability, and integrity. This report is available to the general public.
To find out more about SOC centers, click the button below!
Cloud Security Alliance

Cloud Control Matrix (CCM) is a set of guidelines developed by the Cloud Security Alliance (CSA). CCM is intended to help the cloud service providers assess their security. It is also largely used by cloud consumers to assess security risks that may be associated with a specific cloud service provider.
Some of the key highlights of CCM are:
It contains 16 domains split across 133 control objectives.
It is considered a de-facto standard for cloud security compliance.
It focuses on various other security frameworks, such as ISO 27001, PCI-DSS, and NIST.
Benchmarks/Secure Configuration Guides
Each system that exists and connects to the network or the Internet needs to be secured. While different organizations have different standards that they follow, it is easy to follow the secure configuration guides, which offer a standardized way of configuring systems with an optimal security level. One good example of secure configuration guides is from the Center for Internet Security (CIS), which provides specific security benchmarks.
Platform/Vendor-Specific Guides
Vendors who develop applications or platforms also offer guides for installation and configuration. The guides also include the best practices for installation, configuration, and operational activities, which should be followed by the users. The vendor must provide the best practices to safeguard their products and the customers’ data that resides on their applications and platforms.
Some of the key products that require a high level of security are:
Web Servers
Operating Systems (OS)
Application servers
Network infrastructure devices
Let’s look at each one of them in detail.
Web Server

A Web server is mostly Internet-facing and, therefore, considered to be vulnerable. If an organization is hosting a Web application used by customers and internal users, it is important to harden the Web server so that it is secured with optimal security.
There are a variety of Web servers that are available. Some of the prominent ones are:
Apache
Microsoft Internet Information Services (IIS)
Nginx
CIS provides the set of hardening guidelines for IIS, which cover virtually all aspects of security
set of CIS guidelines for IIS 10.0:
1. Basic Configurations
1.1. Ensure web content is on non-system partition
1.2. Ensure ‘host headers’ are on all sites
1.3. Ensure ‘directory browsing’ is set to disable
1.4. Ensure ‘Application pool identity’ is configured for all application pools
1.5. Ensure ‘unique application pools’ is set for sites
1.6. Ensure ‘application pool identity’ is configured for anonymous user identity
1.7. Ensure WebDav feature is disabled
Other than the CIS guidelines, you may also want to explore guidelines from the Open Source Foundation for Application Security (OWASP) and the application vendor. For example, in the case of IIS, you may want to check the Microsoft Website, which has sufficient guidelines and best practices for hardening and securing IIS.
Operating System (OS)













An operating system is the base platform on which applications run. Even if the applications are secure, if there are security loopholes in the operating system security, they are at a higher risk of exploitation. Therefore, you need to ensure that you secure the operating system before you secure anything else running on it. This is one of the key reasons for several recommendations and guidelines that state that the operating system must be hardened immediately after the installation.
There are several guidelines and recommendations available from the following:
CIS
Department of Defense (DoD) Defense Information Systems Agency (DISA)
Platform vendors
This is an example of recommendation on password setting from CIS:
1 Account Policies
This section contains recommendations for account policies.
1.1 Password Policy
This section contains recommendations for password policy.
1.1.1 (L1) Ensure ‘Enforce password history’ is set to ’24 or more password(s)’ (Scored)
Profile Applicability:
Level 1
Level 1 + BitLocker
Description:
This policy setting determines the number of renewed, unique passwords that have to be associated with a user account before you can reuse an old password. The value for this policy setting must be between 0 and 24 passwords. The default value for Windows Vista is 0 passwords, but the default setting in a domain is 24 passwords. To maintain the effectiveness of this policy setting, use the Minimum password age setting to prevent users from repeatedly changing their password.
The recommended state for this setting is: 24 or more password(s).
Application Server

Application servers are installed and configured to provide certain services. For example, an application server can be configured with a messaging application to manage the flow of emails for an organization. These application servers need to be secured based on CIS’s recommendations and the vendors, such as Microsoft.
An example for Microsoft Exchange Server 2016:
1 Transport
This section contains recommendations that impact messages while they are in transit. The following PowerShell Cmdlet are covered in this section:
Set-SendConnector
Set-SenderFilterConfig
Set-SenderReputationConfig
Set-ReceiveConnector
Set-TransportServer
Set-TransportService
Set-TransportConfig
Set-PopSettings
Set-ImapSettings
1.1 Set ‘Maximum send size – connector level’ to ‘10240’ (Not Scored)
Profile Applicability:
Level 1 – Edge Services Security
Description:
This setting limits the total size of messages at the connector level. This includes the message header, the message body, and any attachments. For internal message flow, Exchange Server uses the custom X-MS-Exchange-Organization-Original Size message header to record the original message size of the message as it enters the Exchange Server organization. Whenever the message is checked against the specified message size limits, the lower value of the current message size or the original message size header is used. The size of the message can change because of content conversion, encoding, and agent processing.
Rationale:
This setting somewhat limits the impact a malicious user or a computer with malware can have on the Exchange infrastructure by restricting the size of incoming messages.
Network Infrastructure Devices
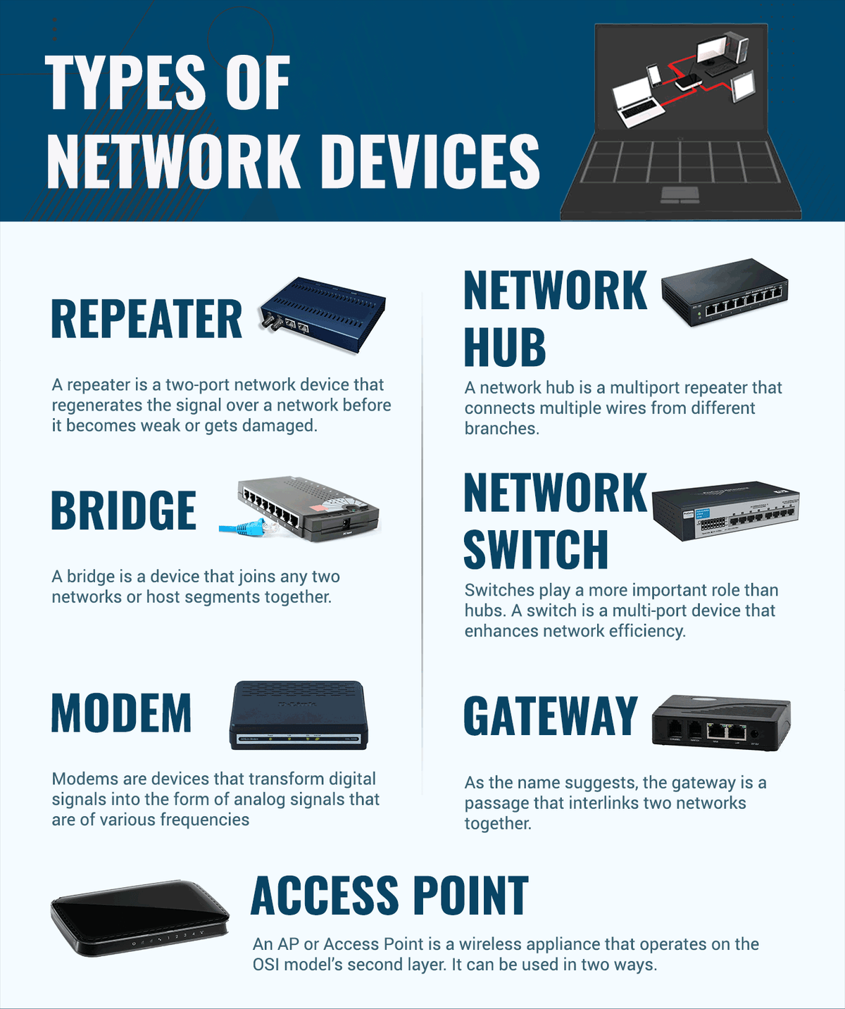
A network can host a variety of devices, such as routers, firewalls, and switches. Each of these devices must be hardened with proper configuration. For example, most organizations deploy a firewall on the edge of their network, then the traffic is routed through the firewall. If the firewall itself is not hardened, this can be a big security lapse, potentially exposing the entire network to outside users.
It is important to note that network devices also have software for their functionality, but these can have vulnerabilities. In several cases, these are exploited. The vendor may detect the vulnerabilities and release a patch to be deployed urgently.
Another major aspect is the manual configuration, which is performed by the administrators. Most often, the manual configuration itself is flawed. For example, the administrator may leave ports open.
Two major entities that have the security guidelines for network infrastructure devices are:
CIS
DoD DISA



